Top 95+ imagen microsoft office memory corruption vulnerability
Introduzir imagem microsoft office memory corruption vulnerability.

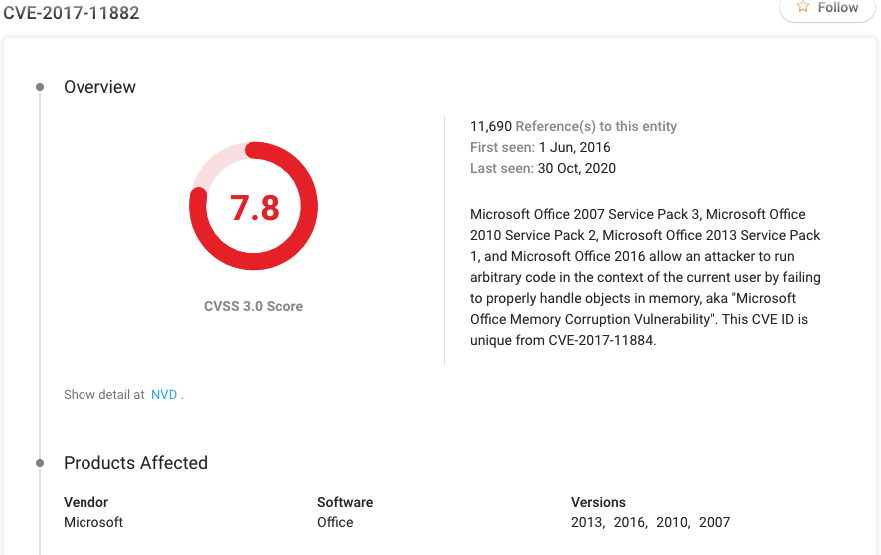
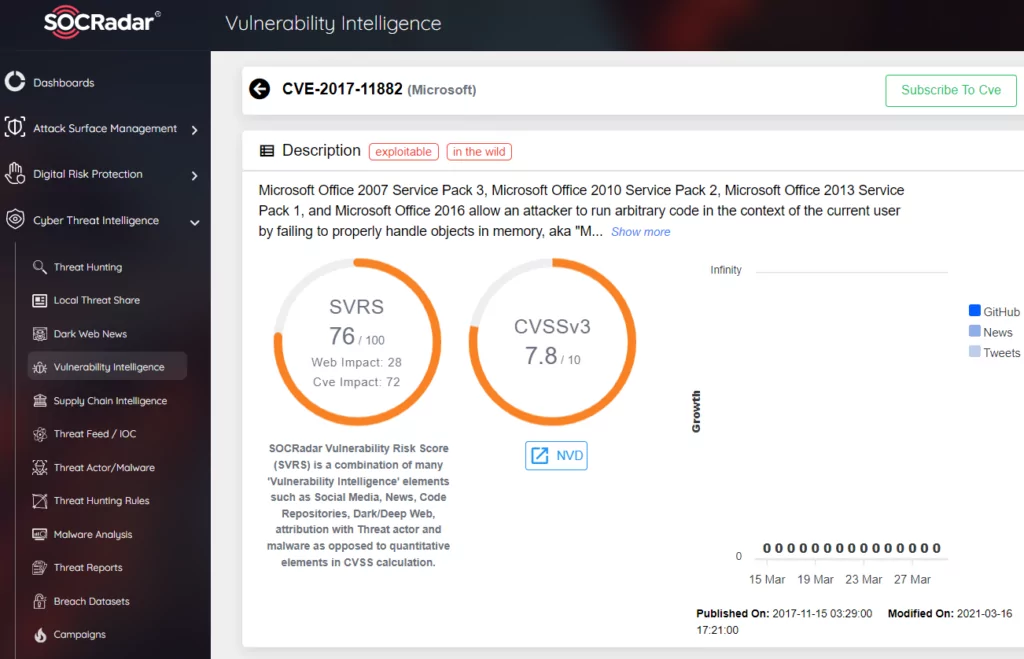
Microsoft Office Memory Corruption Vulnerability (CVE-2017-11882)

Microsoft Office Memory Corruption Vulnerability (CVE-2017-11826)
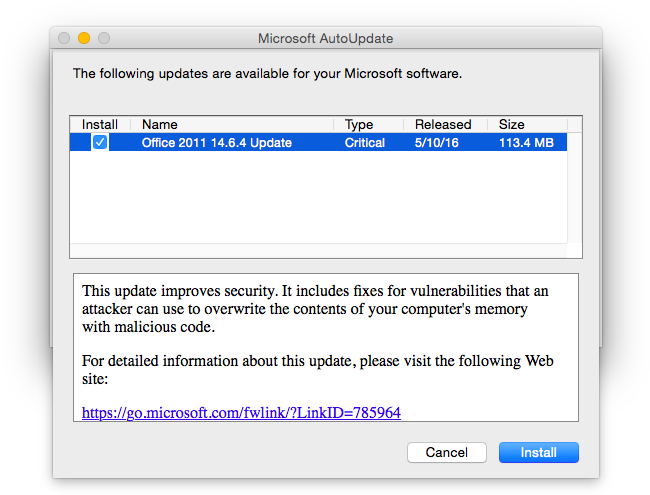
Microsoft Office 2011 Update Patches Memory Corruption Flaws – The Mac Security Blog

0patch fixes Memory Corruption vulnerability (CVE-2022-35742) in Microsoft Outlook 2010 – Born’s Tech and Windows World

Exploit Prevention: Microsoft Office Memory Corruption – YouTube

CVE-2017-11826 – Microsoft Office Memory Corruption Vulnerability – Alert!
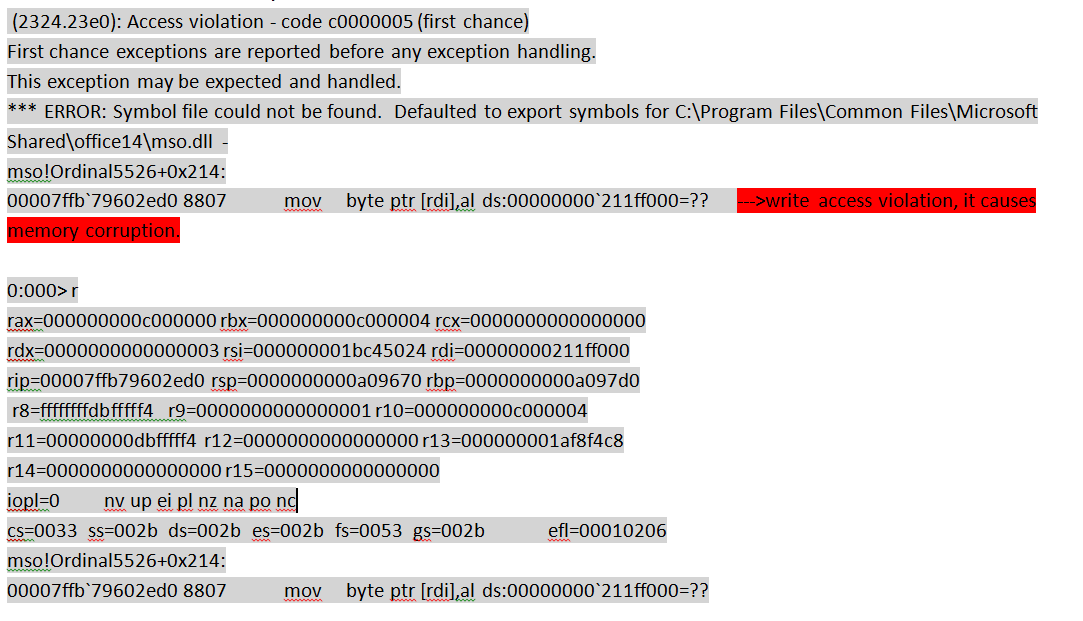
Deep Analysis of CVE-2016-0010 – Microsoft Office RTF File Handling Heap Overflow Vulnerability

Exploit Prevention: Microsoft Office Memory Corruption – YouTube
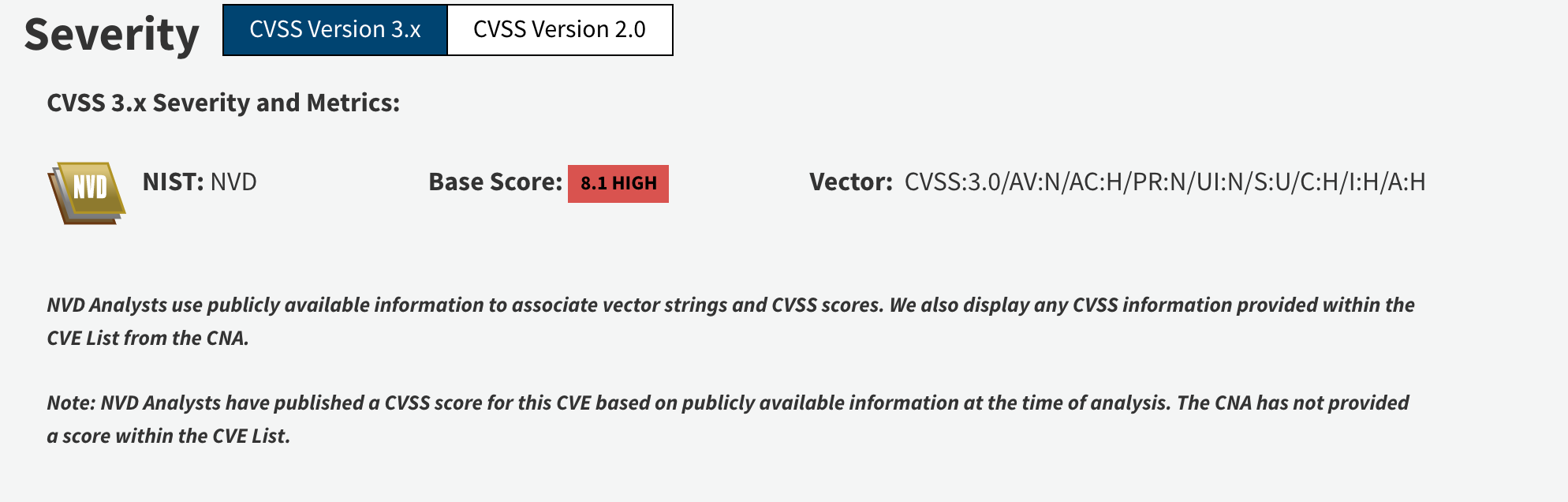
The Most Frequently Exploited Vulnerabilities – SwordSec

CVE-2017-11882: Two-Decades-Old Vulnerability in Microsoft Office Still Actively Leveraged For Malware Delivery – SOC Prime

Microsoft Office Memory Corruption Vulnerability | Cyber Intelligence Advisory | Deloitte New Zealand
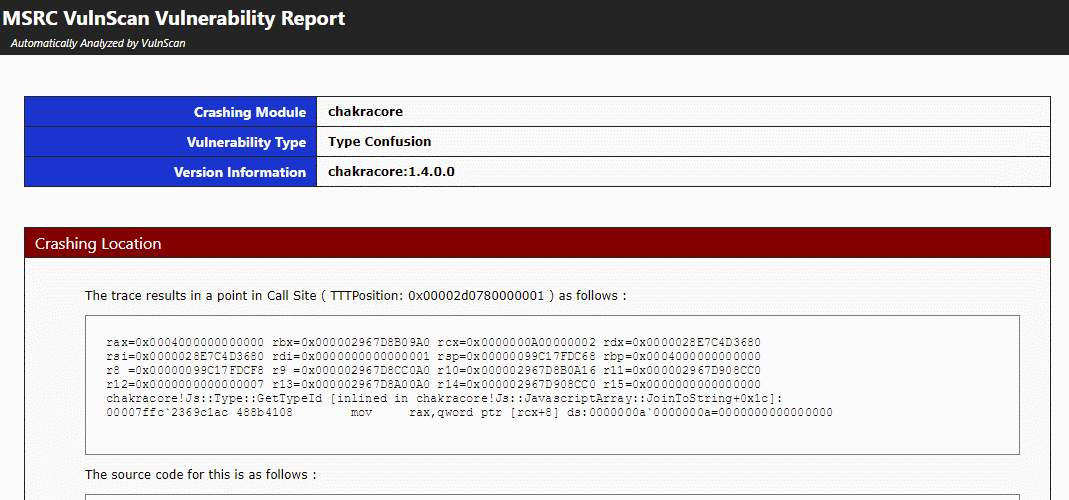
Microsoft Announces New Tool to Investigate Memory Corruption Bugs
CVE-2017-11882 – Do You KNOW This Vulnerability? | KNOW Blog
Microsoft Fixes Security Bugs with Office for Mac 2011 – The Mac Security Blog
Lỗ hổng nghiêm trọng của MS Office cho phép hacker ngầm cài đặt phần mềm độc hại vào máy người dùng – Blog quản trị hệ thống

This years-old Microsoft Office vulnerability is still popular with hackers, so patch now | ZDNET

17-Year-Old MS Office Flaw Lets Hackers Install Malware Without User Interaction

Deep Analysis of CVE-2016-0010 – Microsoft Office RTF File Handling Heap Overflow Vulnerability

Excel Document Delivers Multiple Malware By Exploiting CVE-2017-11882 – Part I | Fortinet Blog

Deep Analysis of CVE-2016-0010 – Microsoft Office RTF File Handling Heap Overflow Vulnerability

Proof-of-Concept released for critical Microsoft Word RCE bug

17-Year Old MS Office Flaw (CVE-2017-11882) Actively Exploited in the Wild – Security News

CVE-2017-11882: Two-Decades-Old Vulnerability in Microsoft Office Still Actively Leveraged For Malware Delivery – SOC Prime

Microsoft Office Spotted with 4 Bugs; MSGraph Bug Receives Patch

Does Follina Mean It’s Time to Abandon Microsoft Office?

Microsoft Patches 17-Year-Old Office Bug | Threatpost

Internet Explorer zero-day surfaces in ‘limited targeted attacks’ | The Daily Swig

Excel Document Delivers Multiple Malware By Exploiting CVE-2017-11882 – Part I | Fortinet Blog
Patch Tuesday: Microsoft Security Updates for May 2021
Microsoft Office MSGraph vulnerability could lead to code execution

CVEs Aiding Initial Access for Ransomware Gangs – Microsoft Office – CyberPlural Blog

Office 365: A guide to the updates | Computerworld

Hackers Exploiting Three Microsoft Office Flaws to Spread Zyklon Malware

MS Office Vulnerabilities Being Actively Exploited by Attackers | Cyware Alerts – Hacker News

Microsoft Patches Memory Corruption Flaw After 17 Years – Vertek
Researchers find four vulnerabilities in Microsoft Office – Adware Guru

Patch Tuesday: Microsoft Security Bulletin April 2020 – SecPod Blog
Beyond Memory Corruption Vulnerabilities – A Security Extinction and Future of Exploitation

Cybersecurity Insights-7 – NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

0patch Blog: Micropatch For Memory Corruption in Microsoft Outlook (CVE-2022-35742)

Fix Critical Word RTF Font Table Heap Bug CVE-2023-21716: Open Source Solution

Uncovering a ChromeOS remote memory corruption vulnerability – Microsoft Security Blog

Top 5 Most Dangerous Microsoft Office Vulnerabilities

Memory Corruption, Memory Corruption, Memory Corruption | by Skybox Security | Medium

Most Q2 Attacks Targeted Old Microsoft Vulnerabilities
Old Microsoft Office Vulnerability Used by Attackers to Deliver RATs

Researchers Released MS Office Zero-Day Vulnerability Details and Exploit Code – Cyber Kendra

BlueHat v17 || Corrupting Memory in Microsoft Office Protected-View S…

CVE-2023-21716: Microsoft Word Remote Code Execution Exploit Explained – cost solution for cybersecurity in Ukraine from IIT Distribution
Microsoft Products as an Attack Vector
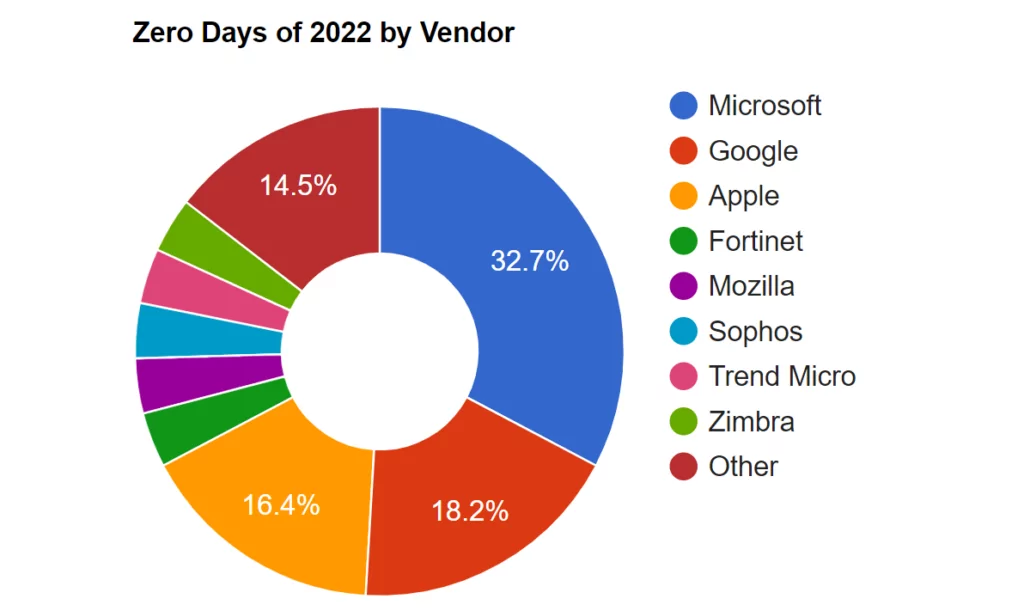
Microsoft Products as an Attack Vector
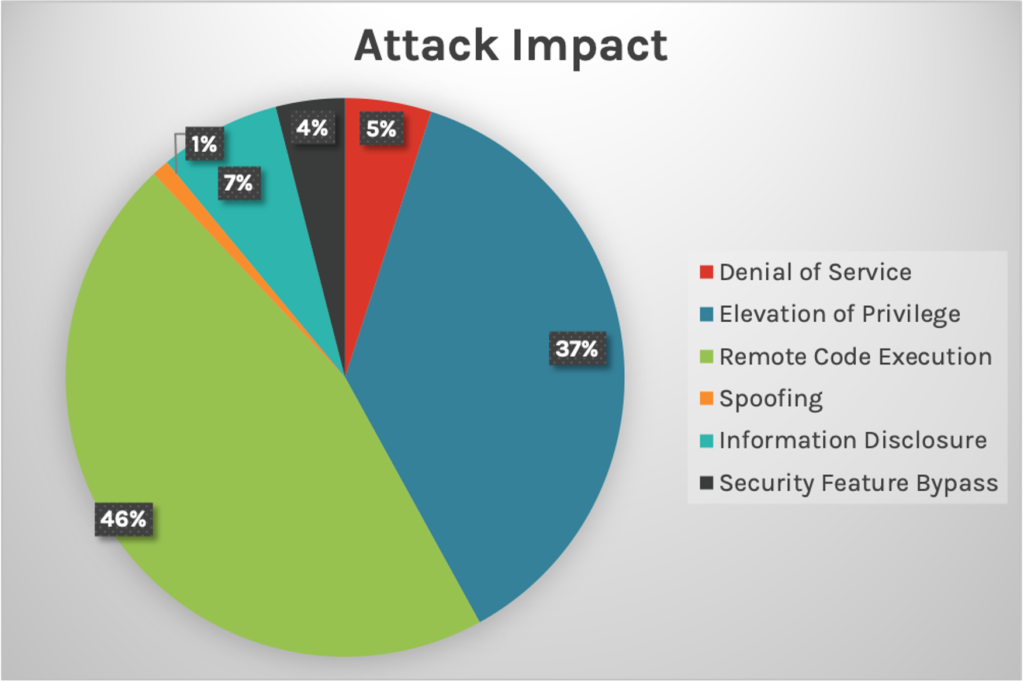
March 2021 Patch Tuesday: Updates and Analysis | CrowdStrike
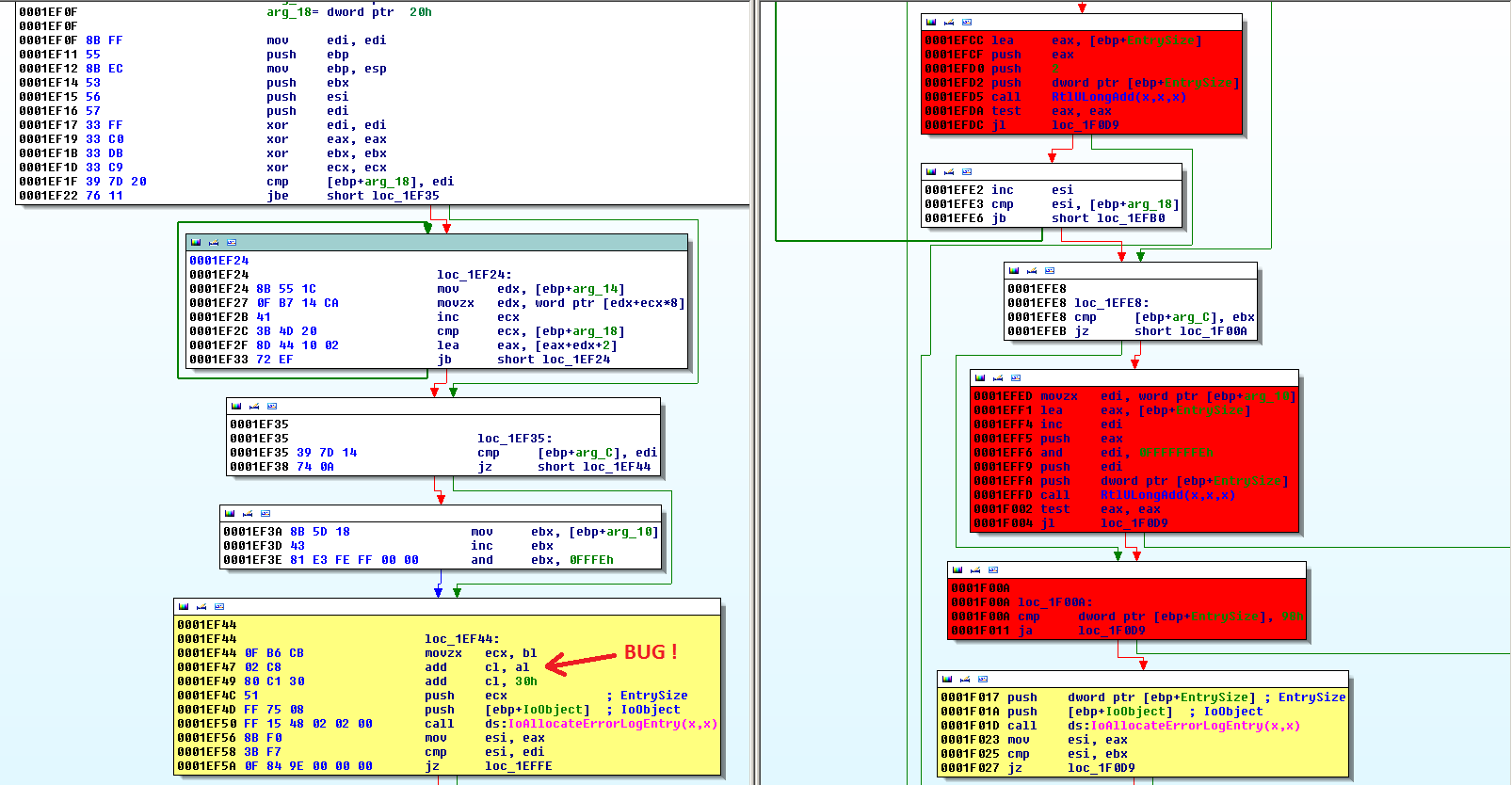
MS15-083 – Microsoft Windows SMB Memory Corruption Vulnerability

Microsoft Patches Three Vulnerabilities Under Attack | Threatpost

Microsoft released a security update to a new Office vulnerability found by 360
Hackers Revive Microsoft Office Equation Editor Exploit

BlueHat v17 || Corrupting Memory in Microsoft Office Protected-View S…
CVE-2018-0845

Microsoft Issues Patches For Severe Flaws, Including Office Zero-Day & DNS Attack

Microsoft Office Memory Corruption Vulnerability | Cyber Intelligence Advisory | Deloitte New Zealand

CVE-2019-1367: Critical Internet Explorer Memory Corruption Vulnerability Exploited In The Wild – Blog | Tenable®

Unit 42 Finds 15 New Vulnerabilities in Microsoft, Adobe, Apple Products

Microsoft Critical Vulnerability CVE-2020-1380 –

BlueHat v17 || Corrupting Memory in Microsoft Office Protected-View S…
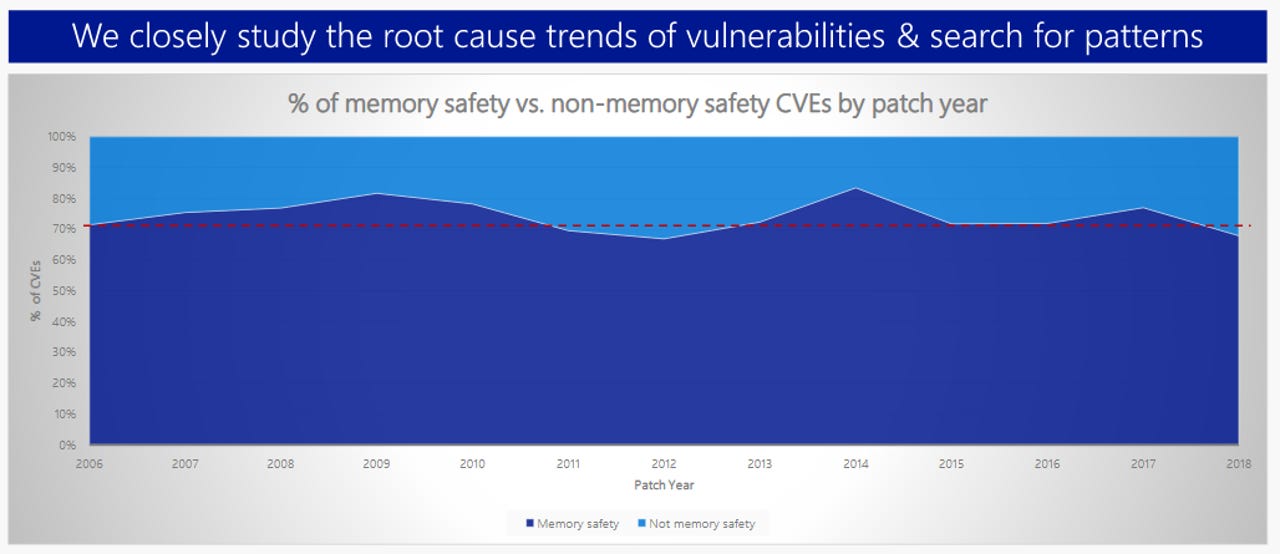
Microsoft: 70 percent of all security bugs are memory safety issues | ZDNET

Microsoft pushes fixes for 44 more vulnerabilities in August Patch Tuesday update – Sophos News

Microsoft’s September 2020 Patch Tuesday Addresses 129 CVEs – Blog | Tenable®

Quick & Dirty Shellcode Analysis – CVE-2017-11882 – YouTube

Uncovering a ChromeOS remote memory corruption vulnerability – Microsoft Security Blog

WINS Server Remote Memory Corruption Vulnerability in Microsoft Windows Server

Microsoft Office the most targeted platform to carry out attacks | CSO Online

Microsoft Issues Security Patch Update for 14 New Critical Vulnerabilities
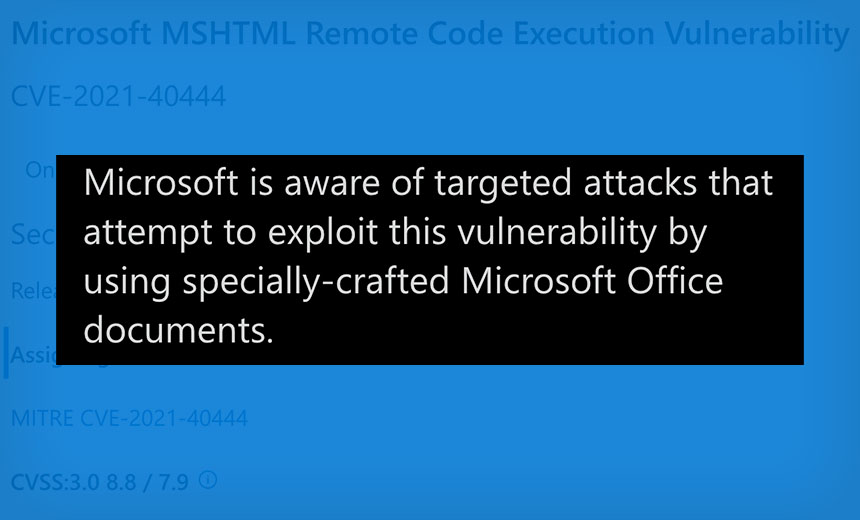
Zero-Day Attacks Exploit MSHTML Flaw in Microsoft Windows

Microsoft Patches Memory Corruption Flaw After 17 Years – Vertek

The Main Vulnerabilities Exploited by Hackers | IT Support LA
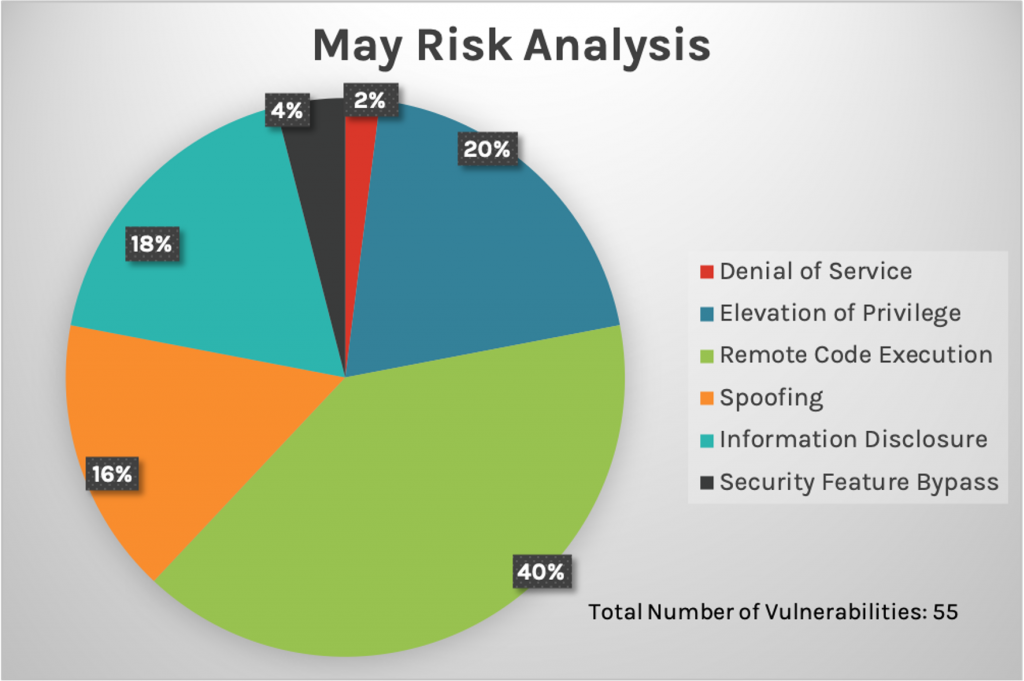
May 2021 Patch Tuesday: Updates and Analysis | CrowdStrike

Infoprive Service Limited (@Infoprive) / Twitter

Patch Tuesday: Microsoft Security Bulletin Summary for September 2020 –
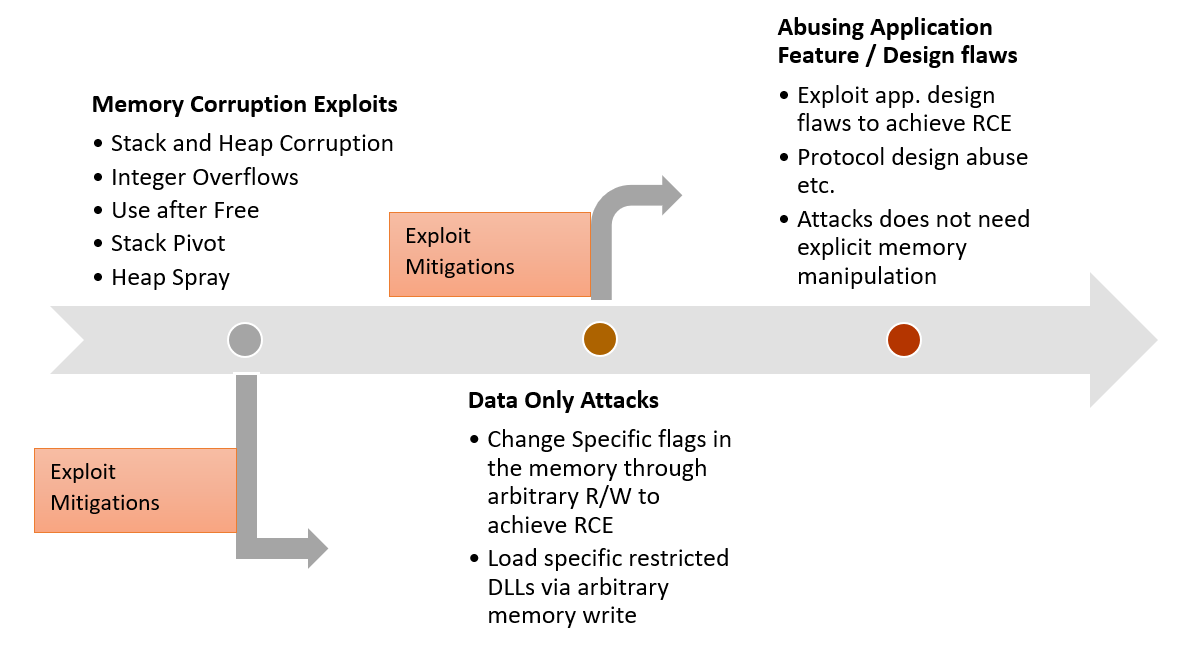
Beyond Memory Corruption Vulnerabilities – A Security Extinction and Future of Exploitation

Hackers have revived a decade-old Microsoft Office exploit – and they’re having a field day | TechRadar

Cảnh báo lỗ hổng mới có mã khai thác
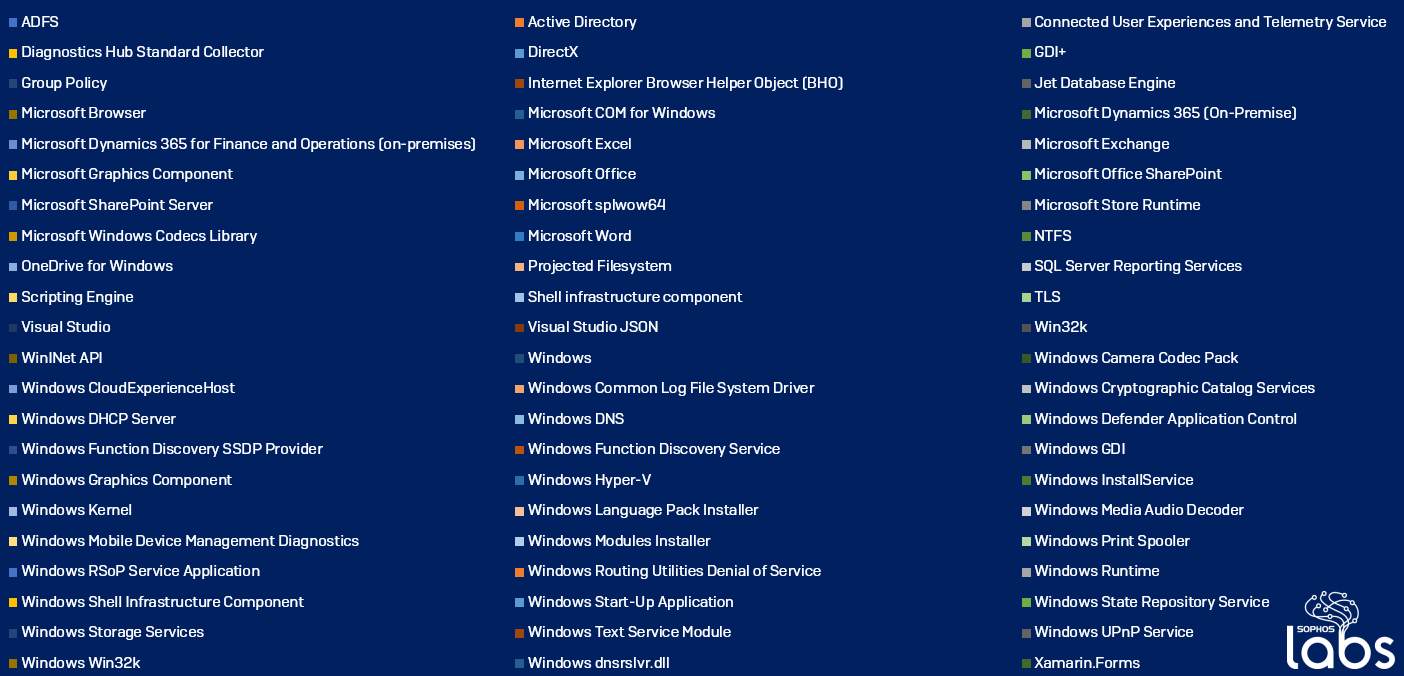
Two dozen criticals among 129 patched vulnerabilities for September, 2020 Patch Tuesday – Sophos News

Microsoft Office products are hacked more than any other platform: Report | Technology News – India TV

Microsoft Office Bug Remains Top Malware Delivery Vector – BlazeGuard

Defense-in-depth – Microsoft Security Response Center

A MS word malware analysis. Recently i was interested in analyzing… | by Nishan Maharjan | Medium
MS15-083 – Microsoft Windows SMB Memory Corruption Vulnerability
ReversingLabs’ YARA rule detects a Cobalt payload exploiting CVE-2017-11882

Patch Tuesday: December 2021 Updates | Kaseya
Malware payloads latest: Microsoft Office macros remain the most frequently used delivery method

Microsoft’s December 2021 Patch Tuesday Addresses 67 CVEs (CVE-2021-43890) – Blog | Tenable®

Microsoft Vulnerability Leads to RAT & Phishing Site | Blog

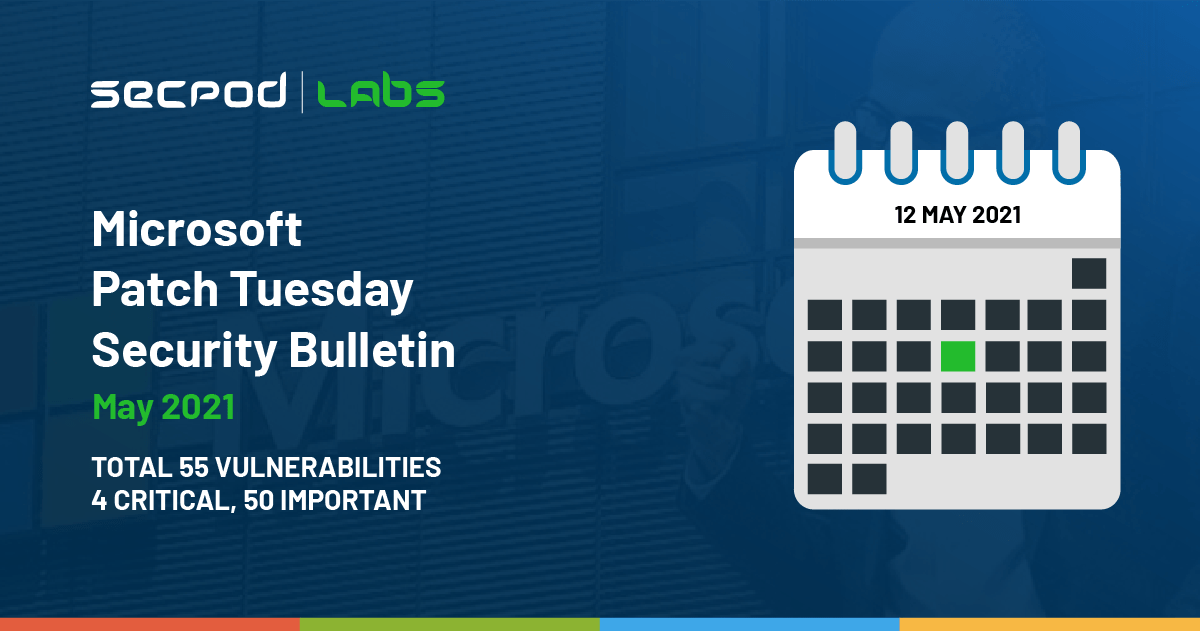
Microsoft Patch Tuesday May 2021 fixes 55 vulnerabilities, including 3 zero-days – ManageEngine Blog

A new Internet Explorer bug can take over your entire PC, so stop using it | PCWorld

This years-old Microsoft Office vulnerability is still popular with hackers, so patch now | ZDNET
Publicaciones: microsoft office memory corruption vulnerability
Categorías: Office
Autor: Abzlocalmx
Reino de España
Mexico





