Tutustu 36+ imagen pasta threat modeling
Jaa kuvia pasta threat modeling.
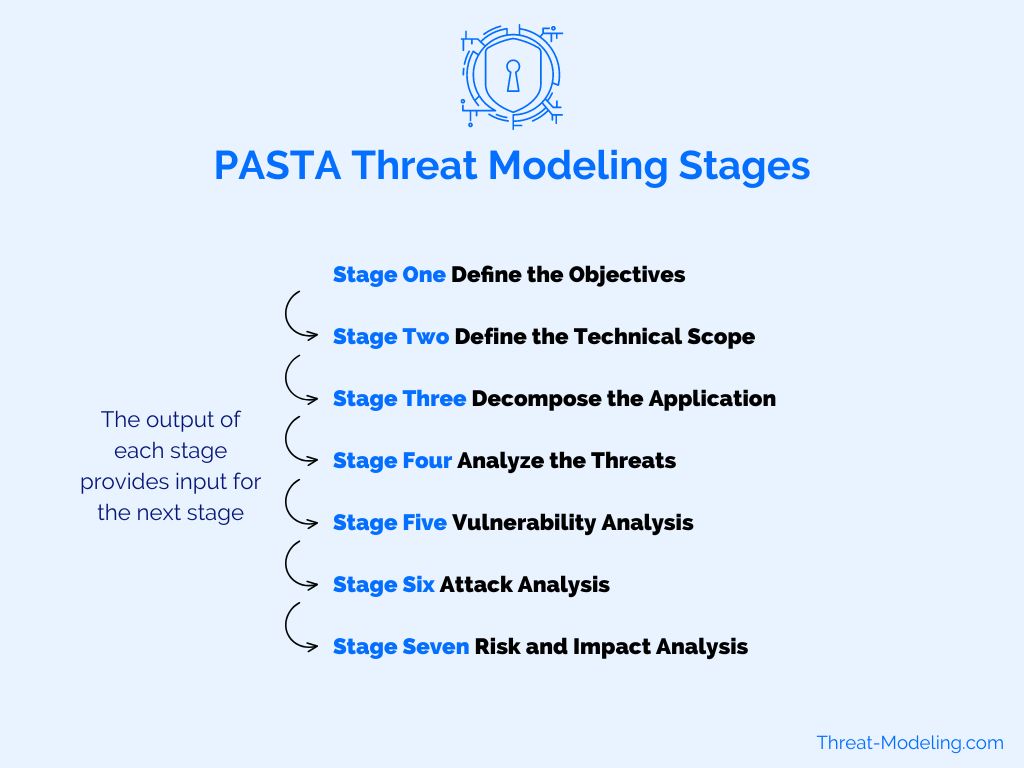
PASTA Threat Modeling
Process for Attack Simulation & Threat Analysis

PASTA Threat Modeling for Cybersecurity | OWASP All Chapters 2020 Presentation – YouTube

Which Threat Modeling Method to Choose For Your Company?

Threat Modeling: 12 Available Methods
Real World Threat Modeling Using the PASTA Methodology

Ο χρήστης VerSprite Cybersecurity Consulting στο Twitter: ”Learn our 7-step PASTA threat modeling methodology that places business impact at the center of our security risk analyses. Download here: /3UD4tJYqN8 — #threatmodeling #infosec #

AppSec EU 2017 Threat Modeling with PASTA by Tony UcedaVelez – YouTube
Threat Modeling w/ PASTA

The PASTA threat model implementation in the IoT development life cycle | Semantic Scholar
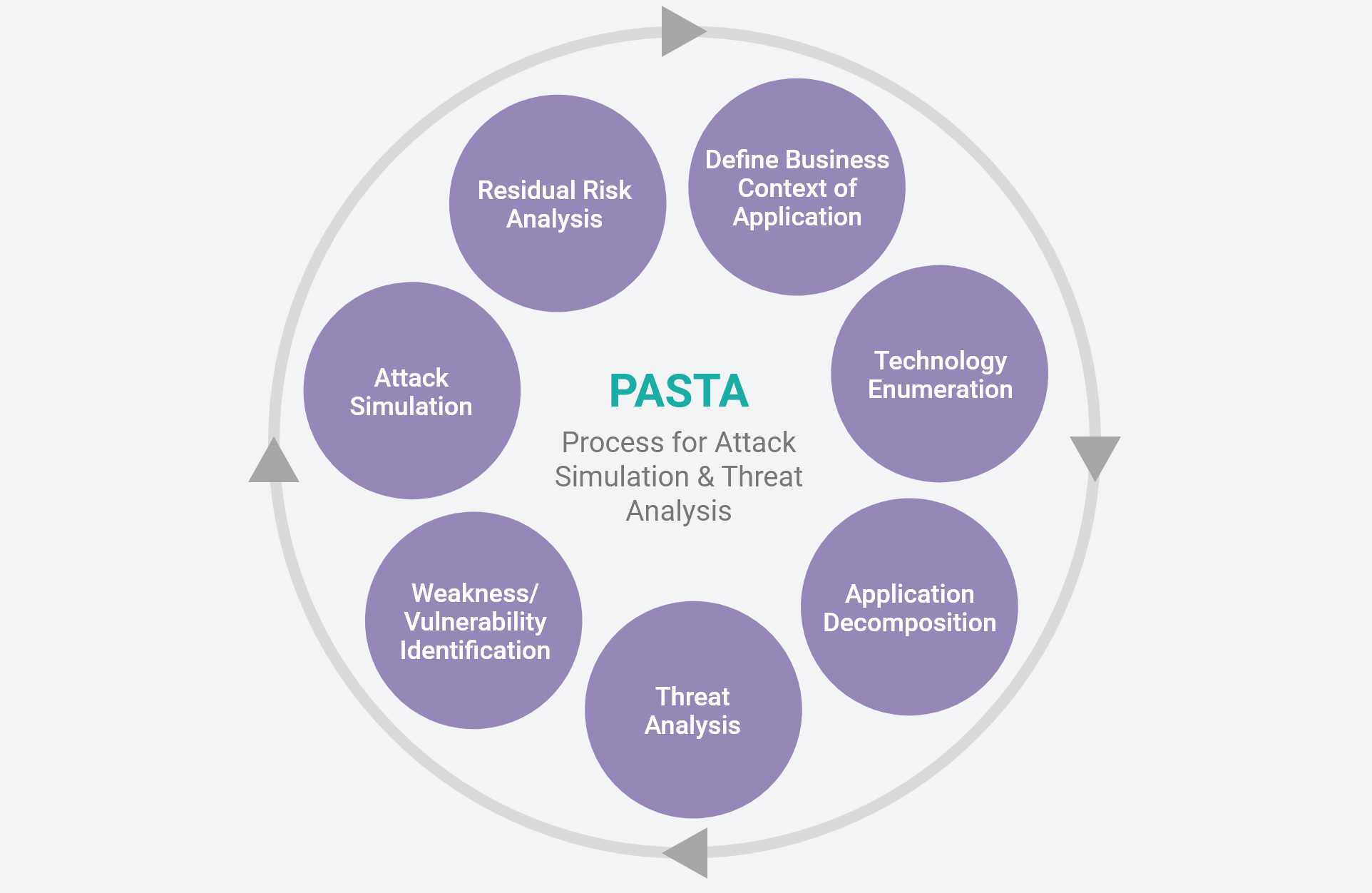
What Is Threat Modeling? | Wind River
OWASP Presentation Template
Application Threat Modeling: Build Risk-Based Threat Models with PASTA

Process for attack simulation and threat analysis | Download Scientific Diagram

6 x Threat Modeling (SDL, STRIDE, DREAD, VAST, TRIKE, PASTA) – YouTube
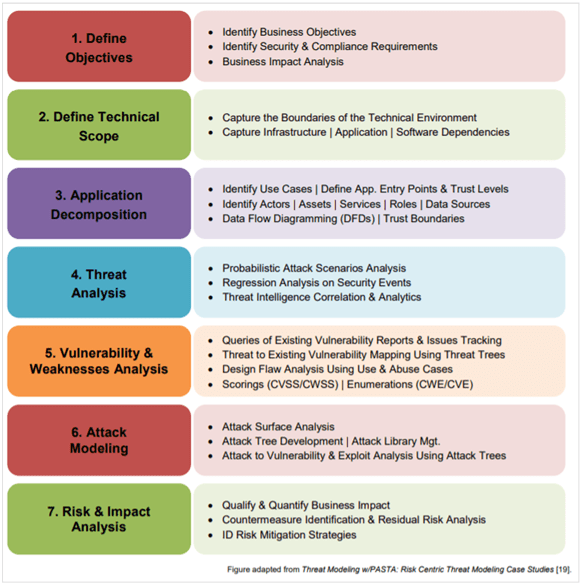
Threat Modelling – Focused Defence for Modern Enterprises

Writing Secure Software: Attack Simulation and Threat Analysis of Banking Malware-Based Attacks
PASTA Threat Modeling – Breaking Down All 7 Steps

PASTA Threat Modeling for Cybersecurity | Threat Modeling Example – YouTube
UNDER ATT&CK: How MITRE’s methodology to find threats and embed counter-measures might work in your organization – (ISC)² Blog
Threat Modeling w/ PASTA

PASTA Threat Modeling

Addressing Cybercrime via PASTA Threat Modeling – Speaker Deck

What is Threat Modeling? Definition, Methods, Example

What Is Threat Modeling? – Cisco
PASTA Threat Modeling – Breaking Down All 7 Steps
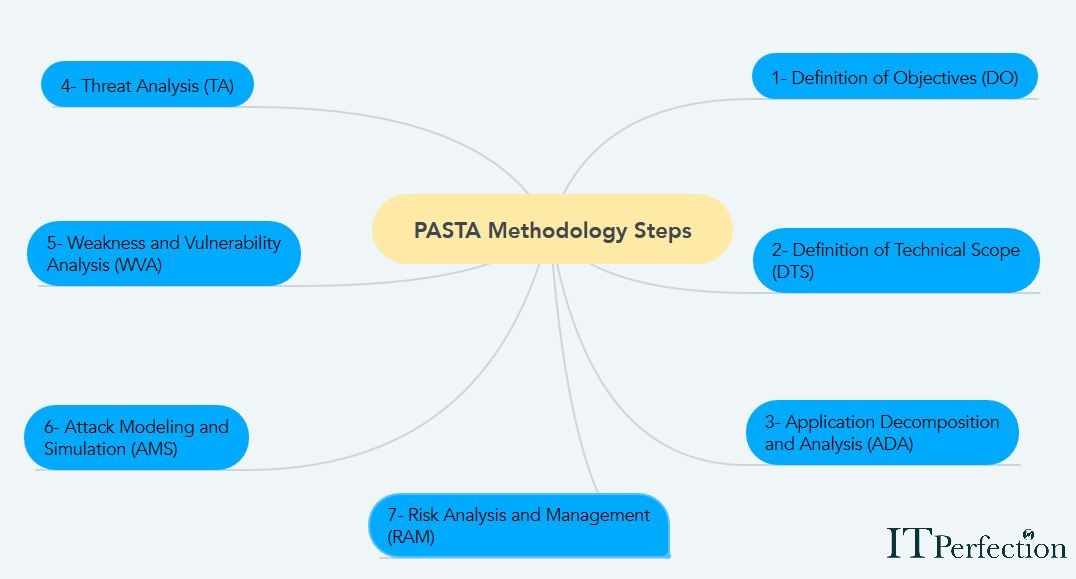
Threat Modeling – CISSP Exaam – ITperfection – Network Security
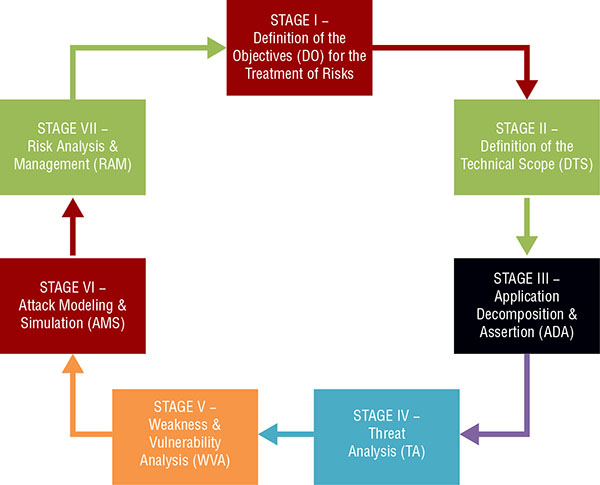
MyClassNotes: Identify Threats with PASTA
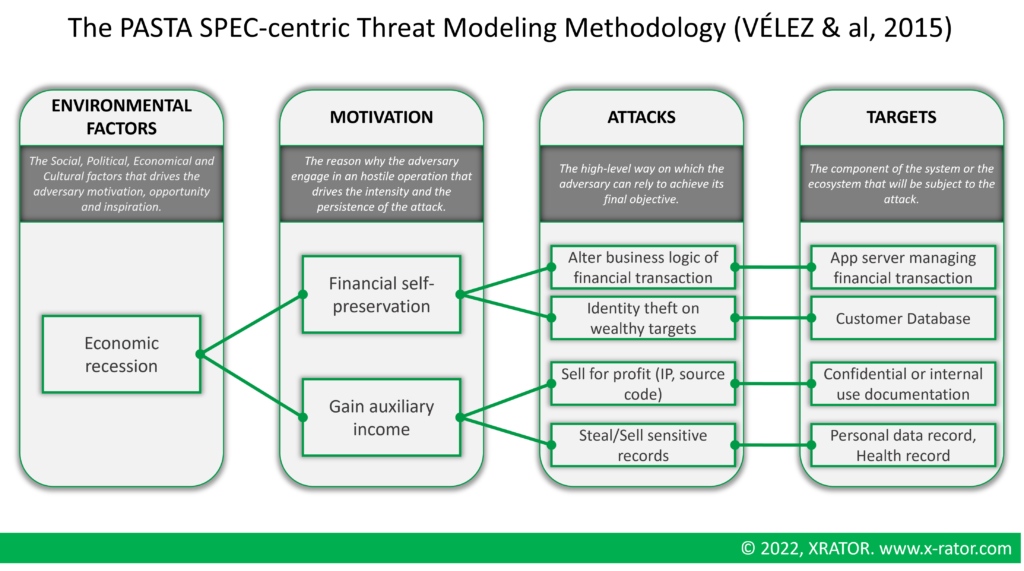
Threat Modeling : from Software Security to Cyber Risk Management – Conquer your risk
What is Threat Modeling: Process, Methodologies & Advantages
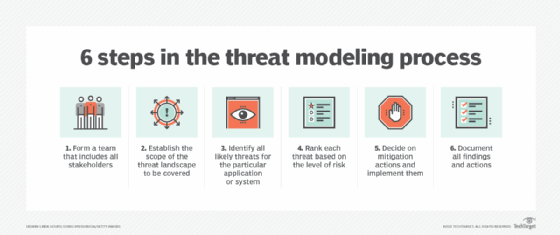
What is threat modeling?
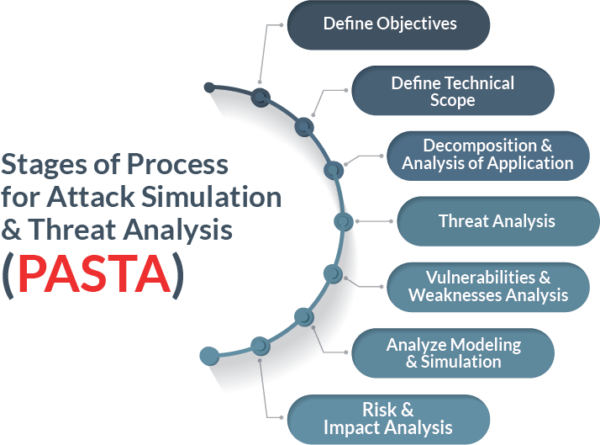
What is Cyber Threat Modeling | Importance of Threat Modeling | EC-Council
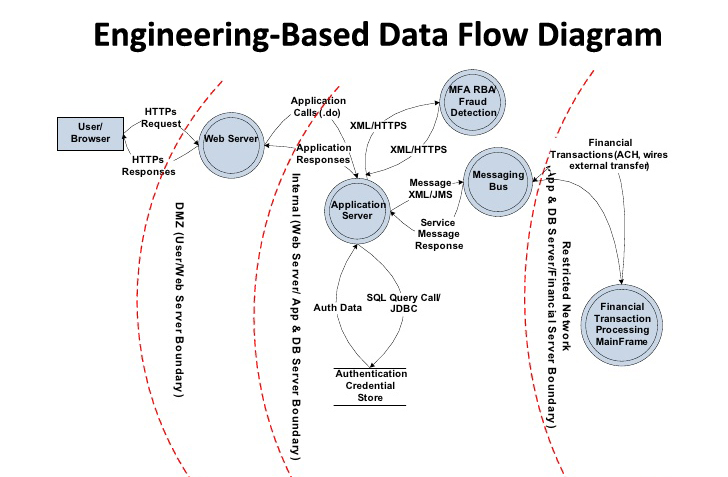
Which Threat Modeling Method to Choose For Your Company?
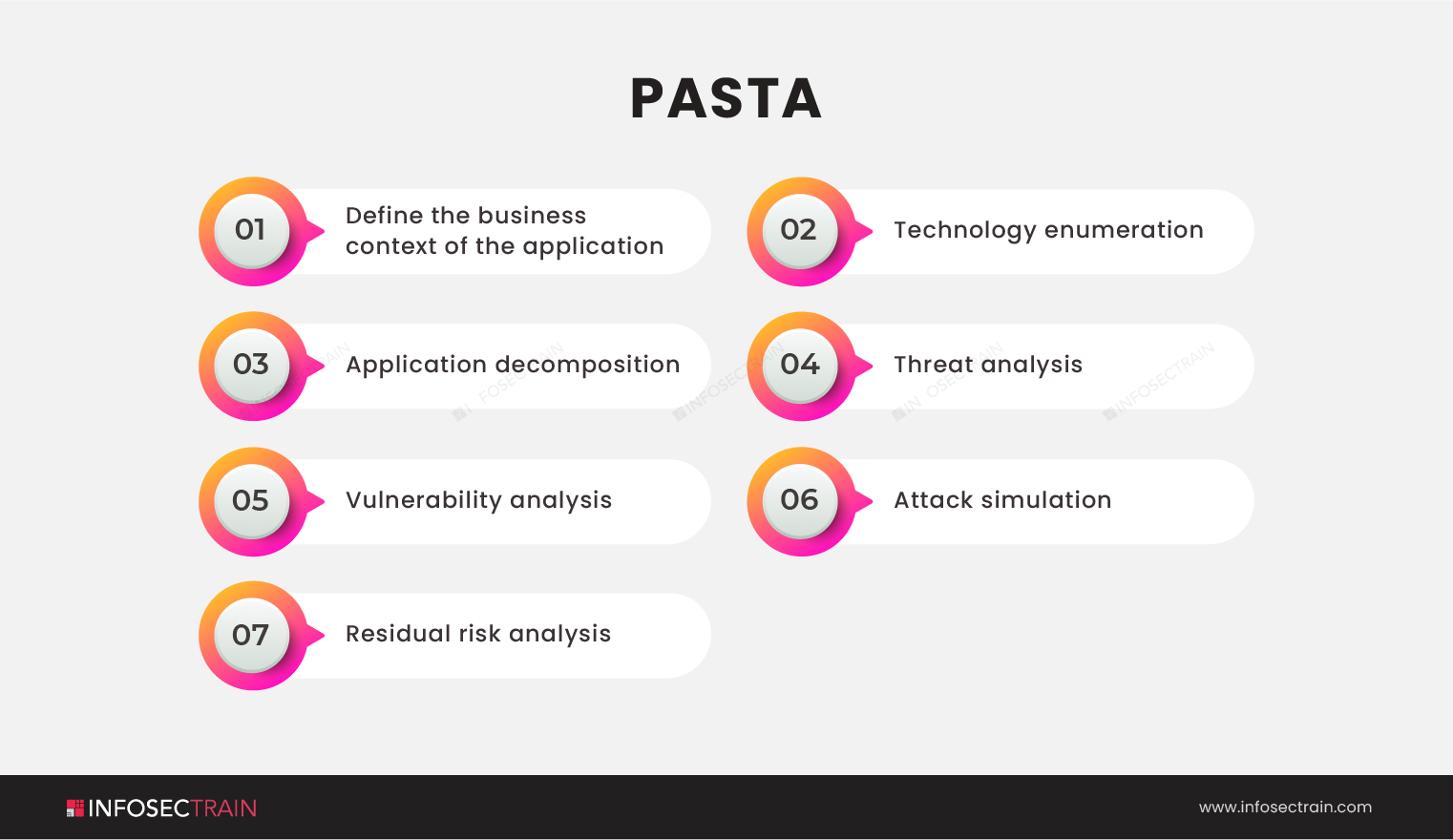
Let’s Discuss Threat Modeling: Process & Methodologies – InfosecTrain
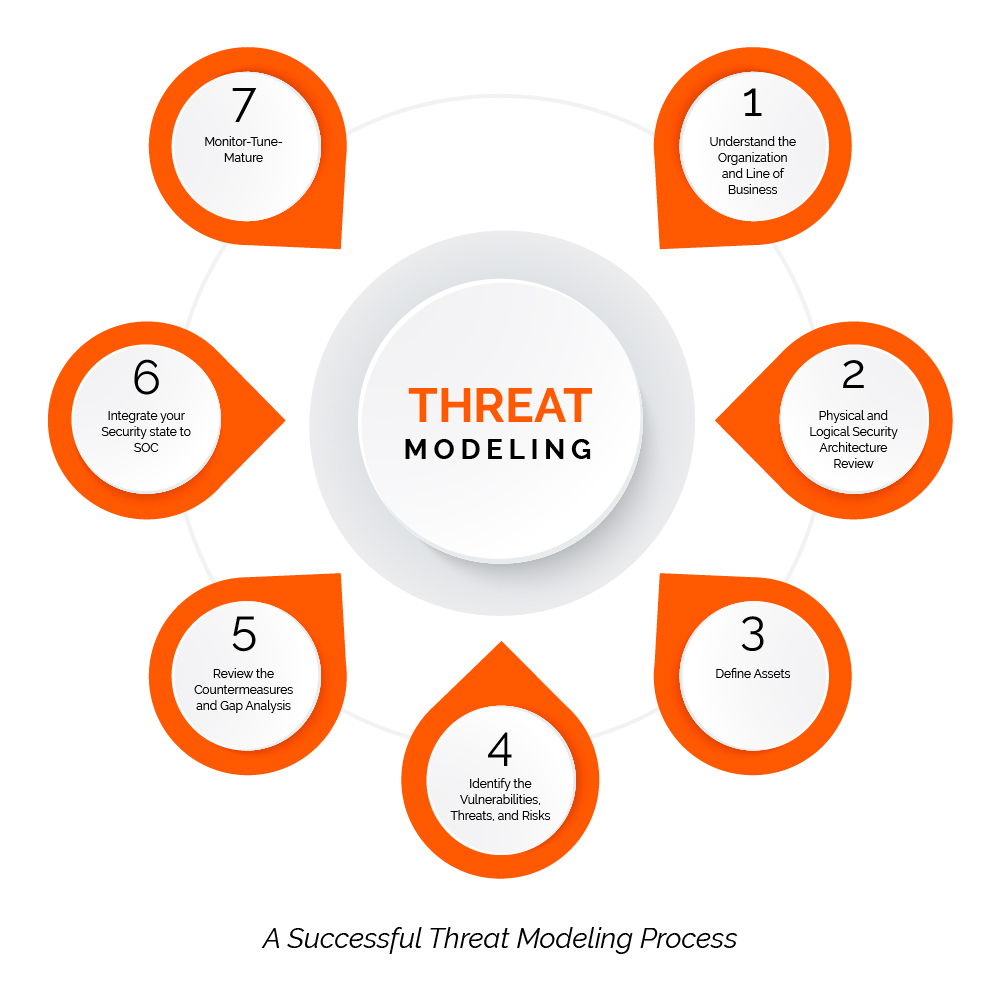
THREAT MODELING TODAY
Threat Modeling w/ PASTA
Viestit: alkuun pasta threat modeling
Luokat: Pasta
Tekijä: Abzlocal.mx/fi
Suomi, Finland





