Descubrir 64+ imagen modelo cyber
Introduzir imagem modelo cyber.
Cyber security management model Source: Designed by the authors | Download Scientific Diagram

The OSI model and cyber attack examples, originally published in… | Download Scientific Diagram

A general model for cyber security | Download Scientific Diagram

The Binary Model of Cybercrime | Download Scientific Diagram
Popular Cybersecurity Models | CompTIA

MMD Model) Cyber End Dragon Download by SAB64 on DeviantArt

What is the Diamond Model of Intrusion Analysis? Why Does It Matter? – TeamT5
The conceptual data model underlying our threatbased cybersecurity risk… | Download Scientific Diagram
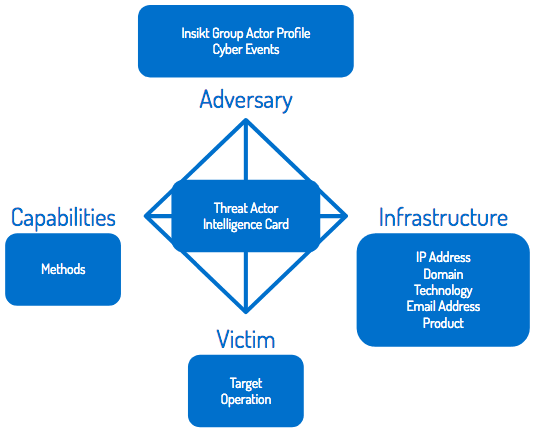
Understanding the Diamond Model of Intrusion Analysis

Cyber samurai Modelo 3D – TurboSquid 1738786

A conceptual model of a cyber-attack to a robot. | Download Scientific Diagram

Cyber Defense Technical reference model (Cyber space architecture… | Download Scientific Diagram

Development of a cyber security risk model using Bayesian networks – ScienceDirect
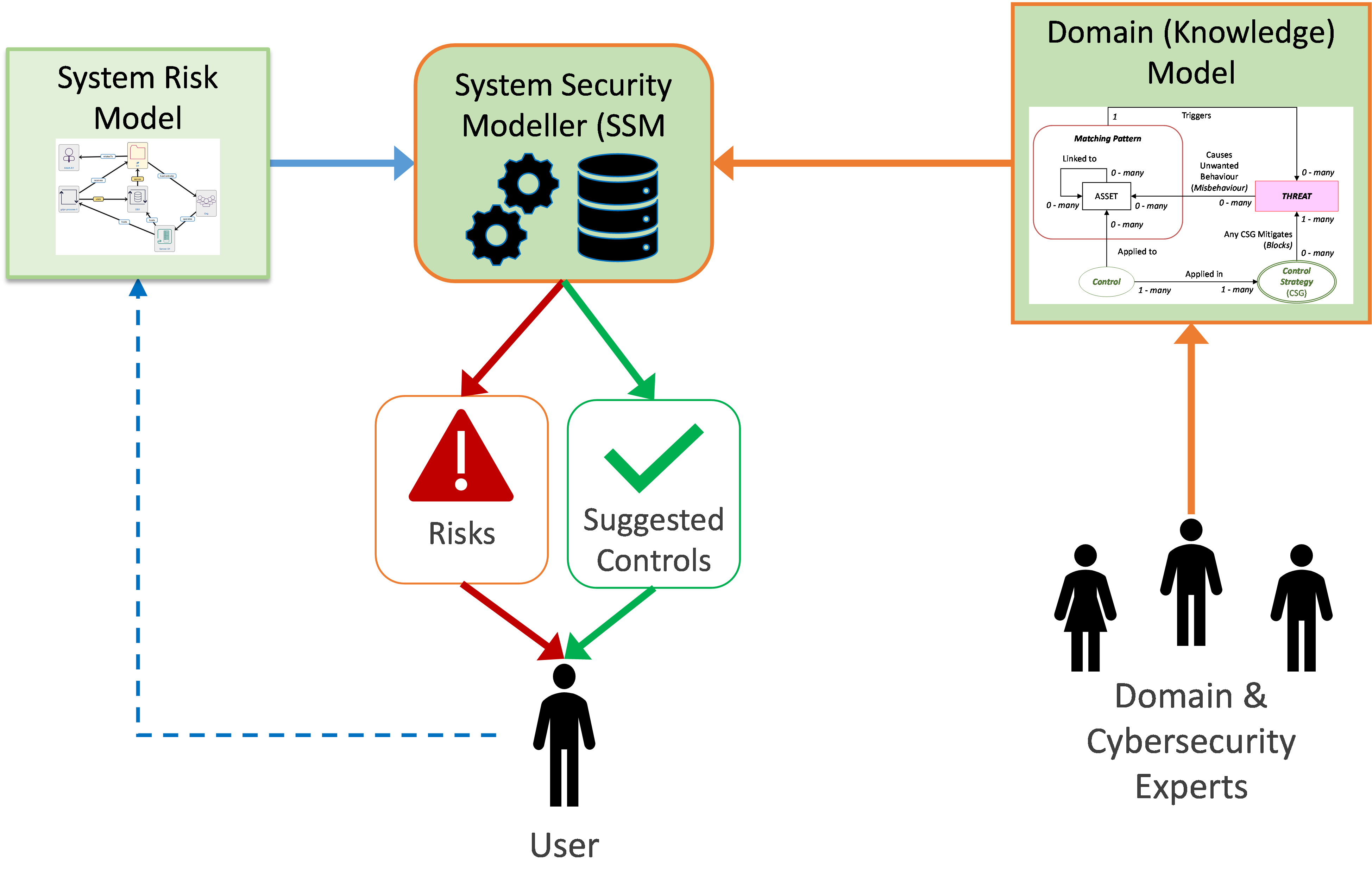
Cyber Security Risk Modelling – ProTego
Space Cyber Bar – 3D Model by malibusan

Proposed model for the cybersecurity management | Download Scientific Diagram
Diamonds or chains – Cyber security – PwC UK blogs
![Capability Maturity Model – InfoSec and cyber intel - Practical Cyber Intelligence [Book] Capability Maturity Model – InfoSec and cyber intel - Practical Cyber Intelligence [Book]](https://www.oreilly.com/api/v2/epubs/9781788625562/files/assets/00278846-490b-48d1-a298-fe3bd165f41a.png)
Capability Maturity Model – InfoSec and cyber intel – Practical Cyber Intelligence [Book]

Why the Hybrid Work Model Increases Risks of Cyber Attacks – Access One

Integral Industrial CyberSecurity , a target operating model | Semantic Scholar

Cyber Security for your Smart Charging System – KPIT

Cyber-Physical System (CPS) model with social domains. | Download Scientific Diagram

Cyber 3D models – Sketchfab

Model Cyber Security Law Pending Final Action By National Association of Insurance Commissioners | Trade Secrets & Employee Mobility

Attribution Models & Frameworks –

SERC TALKS: How Can We Model Cyber Attacks & Systems to Characterize Resilience of Critical Systems? – YouTube
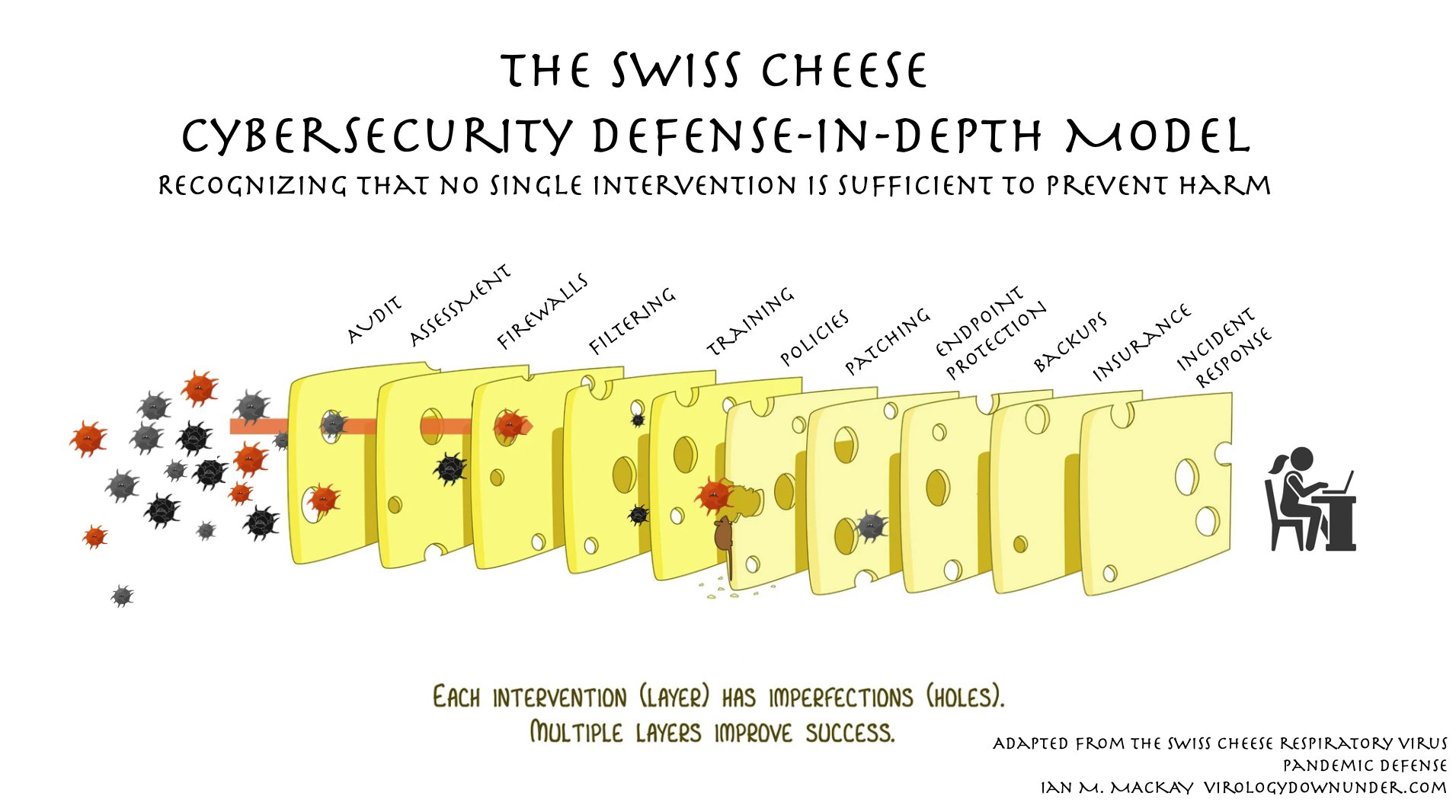
The Swiss cheese cybersecurity model | Andrea Fortuna

How to Build and Enable a Cyber Target Operating Model – JasonHart
![ENGWIND Cyber Helmet - 3D model by engwind (@engwind) [de8eebc] ENGWIND Cyber Helmet - 3D model by engwind (@engwind) [de8eebc]](https://media.sketchfab.com/models/de8eebcc7e4d40b5a816b6c6143e12f8/thumbnails/b3c8df73413340ab8647930fe889916b/93c5b820dedb40bba6be968d8cdd5cc2.jpeg)
ENGWIND Cyber Helmet – 3D model by engwind (@engwind) [de8eebc]

modelo de postagens de mídia social do evento cyber segunda-feira 6239792 Vetor no Vecteezy
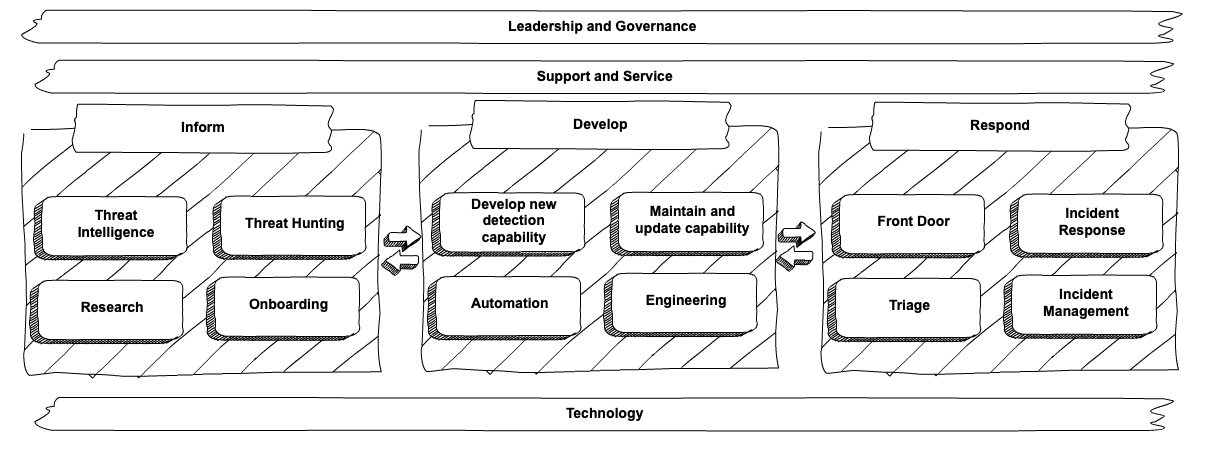
The target operating model

Willis Towers Watson boosts cyber risk model – Commercial Risk

MMD x MMZ Model Preview) Cyber Elf X by NamiSakiwa on DeviantArt

Cyber futuristic console – control desk 3D model – TurboSquid 1933622

Diamond Presentation v2 0: Diamond Model for Intrusion Analysis – Applied to Star Wars’ Battles – YouTube

Conceptual model for identifying and assessing cybersecurity risks | Download Scientific Diagram
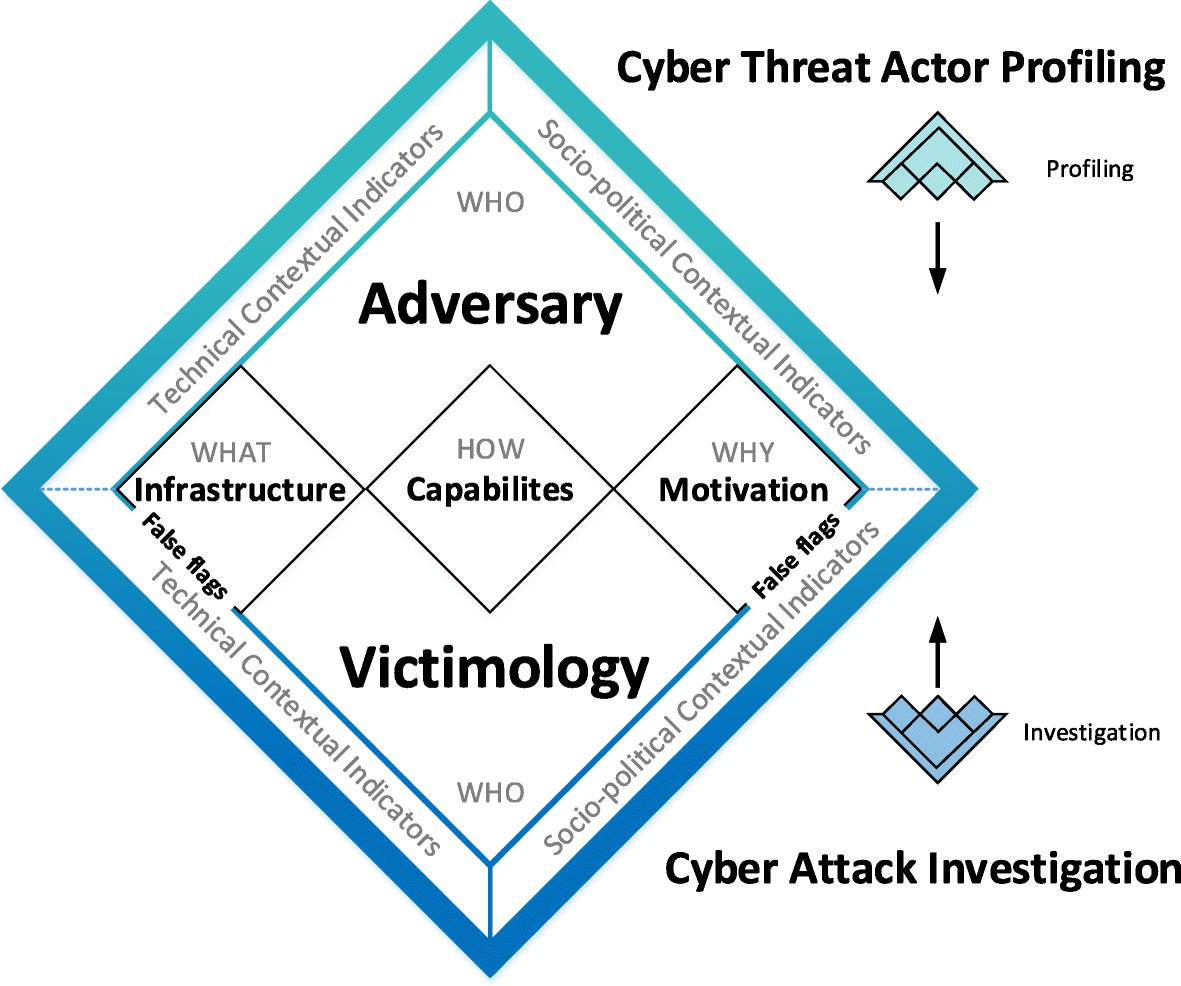
Under false flag: using technical artifacts for cyber attack attribution | Cybersecurity | Full Text
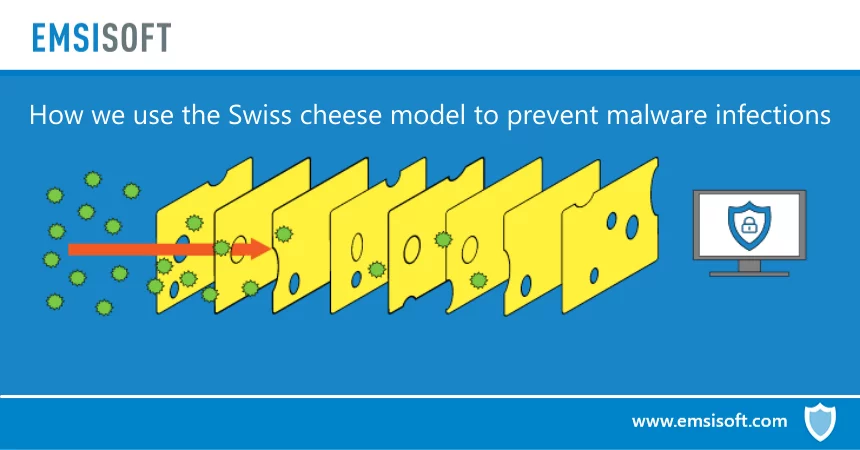
How we use the Swiss cheese model to prevent malware infections
![Capability Maturity Model - InfoSec and cyber intel – Phase A - Practical Cyber Intelligence [Book] Capability Maturity Model - InfoSec and cyber intel – Phase A - Practical Cyber Intelligence [Book]](https://www.oreilly.com/api/v2/epubs/9781788625562/files/assets/28264b16-ace6-476e-ac29-b8db5ebbb69e.png)
Capability Maturity Model – InfoSec and cyber intel – Phase A – Practical Cyber Intelligence [Book]
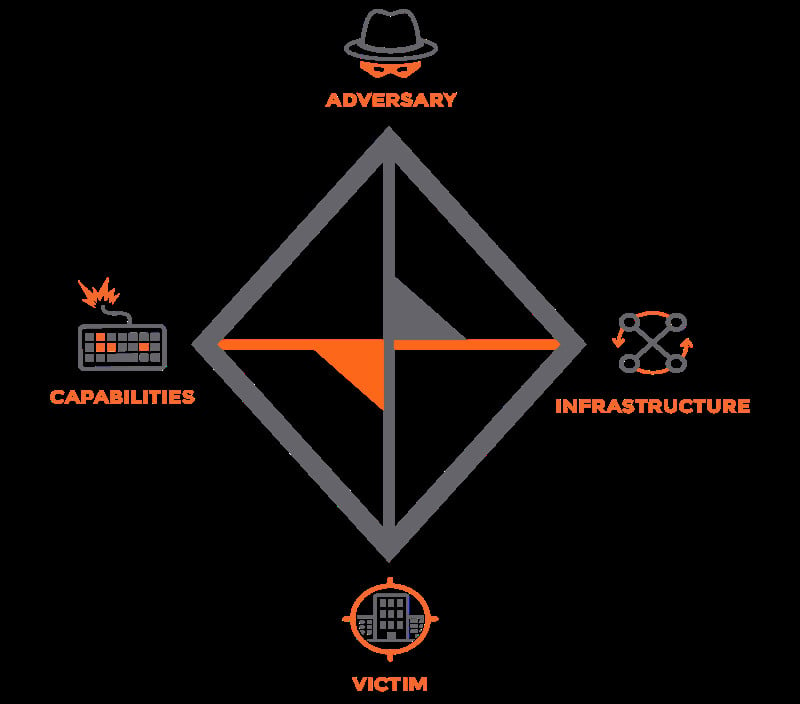
The ABC’s of Cybersecurity Models

Futuristic Fashion Young Woman. Beautiful Young Multi-racial Asian Caucasian Model Cyber Girl In Silver Urban Clothes With Conceptual Hairstyle And Make-up Against Modern Interior In Full Lenght. Sci-fi Poster Style. Stock Photo,

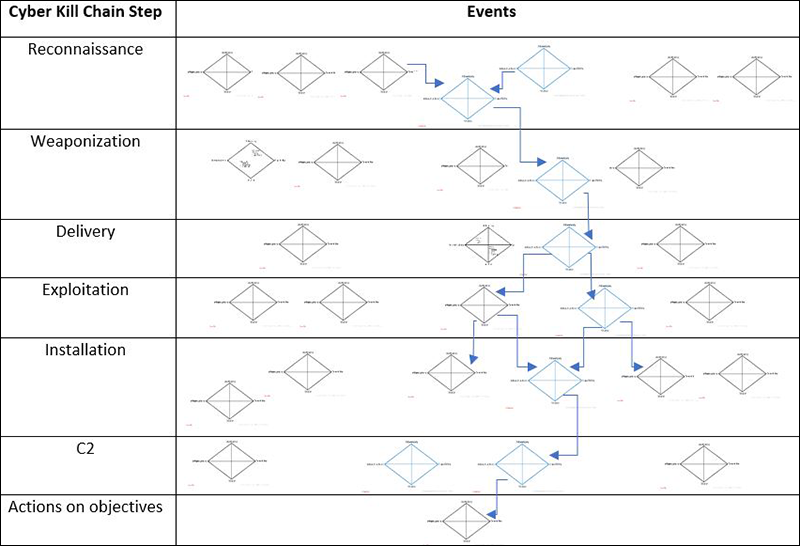
What is the cyber kill chain? A model for tracing cyberattacks | CSO Online

The New Enterprise Security Model: Cyber Risk Management

Girl Assembly Model | Cyber Girl Figure | Mobile Suit Girl | Cyber Hobby | Striker Toy – Girls – Aliexpress

Cyber Kill Chain® | Lockheed Martin

Cybertruck | Tesla

What Is Cyber Risk Modeling? — RiskOptics

Insurers must improve cyber and natural catastrophe modelling: PRA :: Insurance Day

Girl Assembly Model | Cyber Girl Figure | Mobile Suit Girl | Cyber Hobby | Striker Toy – Girls – Aliexpress

A New Cyber Operations Model – Cyber Velocity

OSI Layer based security and incident response model #cybersecurity #infosec #computerscience #computerengineering #riskman… in 2023 | Cyber security, Osi layer, Networking

3D model Cyber Hero – Pants 05 VR / AR / low-poly | CGTrader

The Cyber Security – OSI Model & Attack Vectors #cybersecurity #computerscience #computerengineering #infosec #riskmanagement #encryption #IoT #AI #dataprotection #privacy #hacking #hacker #pentest #tech #datascience #code #coding #python #php …

The Swiss Cheese Model for Cyberattacks – YouTube

Integral Industrial CyberSecurity , a target operating model | Semantic Scholar

Cyber Attack Models: Part 1 | The Lowe Down

Cyber Security Models | Cyber Security Plans | StickmanCyber

Cyber Crazy 2 Modelos – Etsy
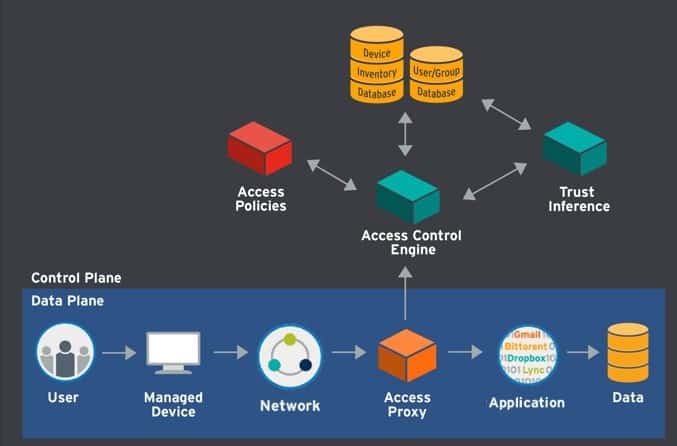
What is the Zero Trust Model of Cybersecurity, Really? | LogRhythm
CyCraft Classroom: MITRE ATT&CK vs. Cyber Kill Chain vs. Diamond Model | by CyCraft Technology Corp | CyCraft | Medium

Traditional approaches to cyber… – Arthur D. Little (ADL) | Facebook

File:Cybersecurity Strategy CS5L Capability Maturity Model – Wikimedia Commons

Cyber ONI Custom Demon – 3D Print Model by LAfactorystore
What is CMMC? The New Cybersecurity Maturity Model Certification from DOD with Latest Updates | CMMI Consultant Blog
Publicaciones: modelo cyber
Categorías: Modelo
Autor: Abzlocalmx